So, Britain has broken off the EU, Brexit , that’s a headline but one thing we never see such headlines for is password and database breaches, what is pbkdf2, the short version, math to protect us when we lose sensitive data like our passwords, before you think this isn’t for you, we are talking about your banking systems that you trust because you always find your balance there, the credit card systems etc.
The long version of this is to simply in lay man terms understanding how they protect you, pbkdf2 is a mathematically proven scrambling solution for your data specifically your passwords to the point where if one gets access to say a bank database or that IT person with access to the database thinks he can share the details with some crooks, the passwords are simply useless.
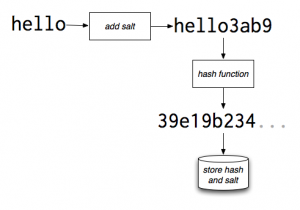 The math genius chaps discovered what is called hashing and put simply it’s that thing that you mix that always gives you the same result without revealing anything about the source or details one entered, compare it to a delicious meal that is so unique it puts your business on the map, your competitors want it but you can happily share the ingredients but they always fail because your method of mixture is your trick. PBKDF2 stands for password based key derivation function, everytime you enter your password it goes into this mathematical engine that makes it look like gibberish, imagine your password is 24, get (24/3132)X3414341 then store the result, when someone sees the result they can never know the password was 24, of course the mathematics is more complex but you get the point.
The math genius chaps discovered what is called hashing and put simply it’s that thing that you mix that always gives you the same result without revealing anything about the source or details one entered, compare it to a delicious meal that is so unique it puts your business on the map, your competitors want it but you can happily share the ingredients but they always fail because your method of mixture is your trick. PBKDF2 stands for password based key derivation function, everytime you enter your password it goes into this mathematical engine that makes it look like gibberish, imagine your password is 24, get (24/3132)X3414341 then store the result, when someone sees the result they can never know the password was 24, of course the mathematics is more complex but you get the point.
How do we keep your passwords safe and why sometimes we don’t have to worry so much about data breaches, well worry a little because they will use your email account for spam, that said your password is in most cases secure unless you are famous and they really want it badly enough to target you that someone starts with ABC…123 and continues going through every possible scenario at which point, asfdafdaffoiwe13, even such a password will be discovered.
Your password is the result of what you enter and some math stuff applied to it to make it unrecognizable to any viewer who has access to the passwords of system, the same way pouring fish oil on chicken can at first taste make it taste like fish but we go further because we know that the bad guys can calculate all possible outcomes of a mixture of two ingredients we add what is known as a salt in this case exactly like the chicken and fish oil, if you get all the chefs in the world, no two can put in exactly the same number of grains of salt so we do the same, we get a random known number (it can be visible) and add it to your password at which point, taking the example above, if we all have a password of 24 but different salts, ((24×5)/3132)X3414341 && ((24×20)/3132)X3414341 will always give us different results where 5 and 20 are different salts for two different users so the final result is different for everyone.
PBKDF2 as a password algorithm goes further than simply adding different known values to passwords to make them universally different, it allows for stirring where the same result can be multiplied against itself a different number of times, the hacker now needs to know the password and the number of times the password has been multiplied against itself but the plot thickens, it is different for every one (the salt) so he cannot come up with all possible guess, he can only focus on one person at a time but the bigger problem is these math geniuses decided that a person’s password output can have 3.4028236692093846346337460743177e+38 options that’s like zillions and who has that time and to add abit of humor, that zillions is before you start stirring by 1000 times.
Incase you are wondering then how do you login, the answer is simple, you have the password (24) which provides the same output but to reverse that you entered 24 is just playing SAW the movie on someones brain.
Truth is we are those geeks who break an egg with a hammer, lol so what do we do we scramble your password with a different ingredient then just for fun we stir it so many times to the point that the first two ingredients are lost way back but also the result for any similar input is the same and that is why you need to know pbkdf2, the math that can make a password of abcd look like rocket science to any on looker.
A parting point, pbdf2 isn’t the only math algorithm (mixing method) but the general principle is the same when it comes to iterative password hashing with salting.
